
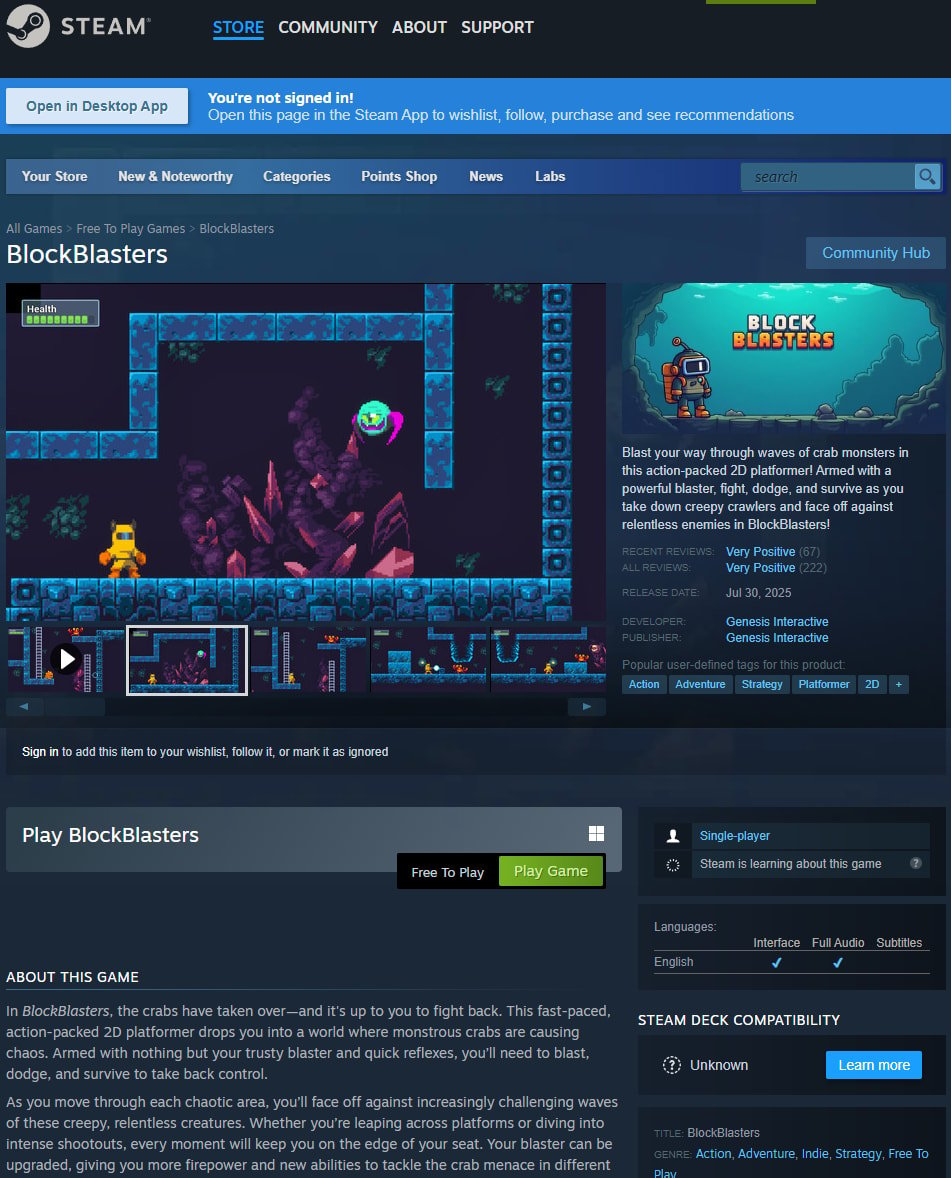
A gamer seeking financial support for cancer treatment lost $32,000 after downloading from Steam a verified game named Block Blasters that drained his cryptocurrency wallet.
Block Blasters is a 2D platformer that was available on Steam for almost two months, between July 30 and September 21. The game was safe until August 30, when a cryptodrainer component was added.
Published by developer Genesis Interactive and no longer on Steam, the retro-styled game was a free-to-play title promising fast-paced action on responsive controls, and had a few hundred ‘Very Positive’ reviews on the gaming platform.
The malicious component in the game was revealed during a live fundraising from video game streamer RastalandTV, who was trying to raise funds for life saving treatment against stage 4 high-grade sarcoma.
The gamer also started a GoFundMe crowdsourcing campaign to receive donations. At the time of writing, completion of the goal is at 58%.
As the Latvian gamer explains, he lost more than $32,000 after downloading a verified game on Steam.
Source: Internet Archive
Crypto investigator ZachXBT told BleepingComputer that the attackers appear to have stolen a total of $150,000 from 261 Steam accounts.
VXUnderground security group, who has also been following the attack, reports a higher victim count of 478, and published a list of usernames, urging their owners to immediately reset their passwords.
Reportedly, these people were explicitly targeted after being identified over Twitter for managing significant cryptocurrency amounts, and were presumably sent invitations to try out the game.
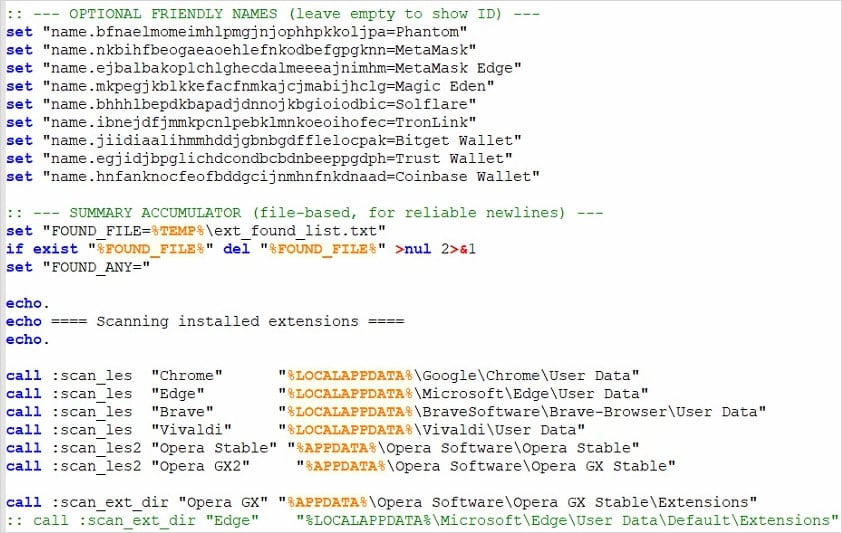
A group of researchers published a brief report detailing the dropper batch script that performs environment checks before it collects Steam login information along with the victim’s IP address, and uploads the data to a command and control (C2) system.
GDATA researcher Karsten Hahn also documented a Python backdoor, and a StealC payload, used alongside the batch stealer.
Source: @struppigel | X
Investigators also highlighted an operational security failure where the attackers left their Telegram bot code and tokens exposed.
There are unconfirmed reports that OSINT experts participating in the hunt identified the threat actor as an Argentinian immigrant living in Miami, Florida.
BleepingComputer has contacted Valve for a comment on Block Blasters and the alleged inaction following multiple reports, but we have not received a response by publication time.
The Block Blasters incident is not an isolated one on Steam. Similar cases earlier this year include the Chemia survival crafting game, Sniper: Phantom’s Resolution, and PirateFi, all of which infected unsuspecting victims with information-stealing malware.
If you have installed Block Blasters on your computer, it is recommended to reset your Steam passwords immediately and move your digital assets to new wallets.
In general, it is advisable to be cautious with Steam games that have a small number of downloads and reviews, and also titles in ‘beta’ development stage, as those can hide malware payloads.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
