
Welcome From Renewablesradar
Radar is a technology that uses radio waves to detect and track the position, speed, and movement of objects.
Real-Time Location Intelligence to Power Smarter Apps and Experiences.
Radar is a system that uses radio waves to detect and monitor the location, speed, and direction of objects.
Real-time object detection and tracking.
Accurate tracking in all conditions.
Real-time location awareness.
Instant detection and response
Enhanced visibility and precision.
Improves tracking accuracy instantly.

LATEST
- Computing: Research and Innovation for Consumer AI ProfitabilityThere is a recent report by Menlo Ventures, 2025: The State of Consumer AI, stating that, “More than half of American adults (61%) have used AI in the past six months, and nearly one in five rely on it every day. Scaled globally, that translates to 1.7–1.8 billion people who have used AI tools, with 500–600 … Read more
- Explore the World Through Architecture: Iconic Styles Across ContinentsThere are various ways to study culture, like its culture and food, but perhaps nothing tells as much about a culture as the buildings it creates. There is something about architecture that keeps on fascinating, be it the soaring domes in Istanbul to the clean geometric lines characteristic of Tokyo. Whether you are interested in … Read more
- A Node.js-Powered App in Record TimeIn today’s developer case study, speed to market matters. The faster and better you can create a working application, the greater the chances of success. Node.js rapid app, through its flexibility, ease, and strong ecosystem, is rapidly becoming one of the top tools for setting development on a fast trajectory and evolving from delivery boy … Read more
- Open vs. closed models: AI leaders from GM, Zoom and IBM weigh trade-offs for enterprise useWant smarter insights in your inbox? Sign up for our weekly newsletters to get only what matters to enterprise AI, data, and security leaders. Subscribe Now Deciding on AI models is as much of a technical decision and it is a strategic one. But choosing open, closed or hybrid models all have trade-offs. While speaking … Read more
- Would you let AI plan your holiday itinerary?In his latest column, Jonathan McCrea is striking a lighter tone and telling us how AI has become his ideal travel companion. I’m heading away for a couple of weeks with the family. We’re going through the packing list now. Underwear, Calpol, flip flops, emergency sugar rations (for me, to be clear). The most important … Read more
Feature your latest articles
This sub headline is a text block global style that is larger and bolder.

She left SIA to follow her passion for polymer clay—now her workshops draw thousands
View Article
The Fork-It-and-Forget Decade – O’Reilly
View Article
Charting a Path Through Education Data In 2025
View ArticleKNOW MORE

A Compromise Worth Making (For Some)
There is one aspect of the iPhone Air that’s closer to the Pro devices than the standard iPhone 17, and that’s the performance. This is due to the fact that the iPhone Air has the same A19 Pro chip as the iPhone 17 Pro and Pro Max, rather than the A19 chip offered by the

OpenAI accelerates Project Stargate with 5 new AI data centers across the US
Comezora/Moment via Getty Images Follow ZDNET: Add us as a preferred source on Google. ZDNET’s key takeaways The data centers will collectively provide 5.5 gigawatts of power. They’re the latest phase of the so-called Project Stargate. Data centers require massive quantities of water for cooling. OpenAI is pushing forward with its mission to power increasingly large AI
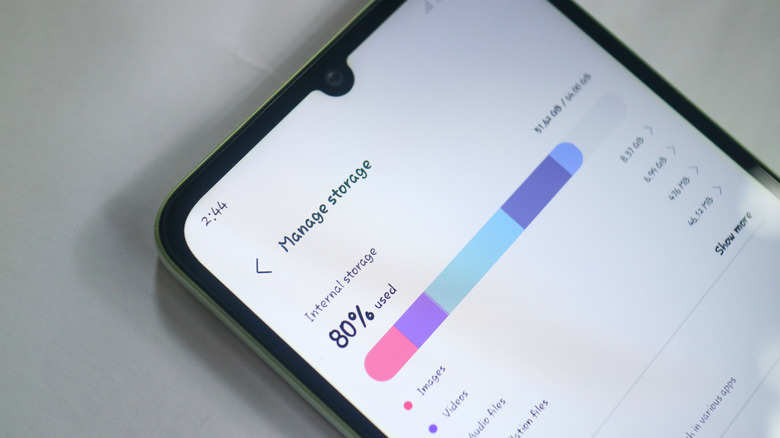
Stop Uninstalling Your Android Apps When You Need Space
eRHa Lens/Shutterstock We’ve all been there. You’re browsing Google Play to download new Android apps or taking photos and videos while out and about, and you see a pop-up on your phone. “Memory full,” it says, or some other variation. This can be a really troubling issue

Microsoft finally squashed this major Windows 11 24H2 bug – one year later
Elyse Betters Picaro / ZDNET Follow ZDNET: Add us as a preferred source on Google. ZDNET’s key takeaways Microsoft has fixed a Windows 11 24H2 bug affecting facial scans. Impacted users are no longer blocked from installing 24H2. Three reported issues with 24H2 still need to be resolved. Microsoft has squashed a long-standing bug in

Google’s AI Mode Sees What You See And Provides Help In Real-Time
Tada Images/Shutterstock Google unveiled Search Live at I/O 2025, a new AI product that brings the multimodal AI capabilities of Project Astra to Google Search on mobile phones. Put differently, Search Live also allows the AI to see what you see in the real world in addition















