Welcome From Renewablesradar
Radar is a technology that uses radio waves to detect and track the position, speed, and movement of objects.
Real-Time Location Intelligence to Power Smarter Apps and Experiences.
Radar is a system that uses radio waves to detect and monitor the location, speed, and direction of objects.
Real-time object detection and tracking.
Accurate tracking in all conditions.
Real-time location awareness.
Instant detection and response
Enhanced visibility and precision.
Improves tracking accuracy instantly.

LATEST
- Computing: Research and Innovation for Consumer AI ProfitabilityThere is a recent report by Menlo Ventures, 2025: The State of Consumer AI, stating that, “More than half of American adults (61%) have used AI in the past six months, and nearly one in five rely on it every day. Scaled globally, that translates to 1.7–1.8 billion people who have used AI tools, with 500–600 … Read more
- Explore the World Through Architecture: Iconic Styles Across ContinentsThere are various ways to study culture, like its culture and food, but perhaps nothing tells as much about a culture as the buildings it creates. There is something about architecture that keeps on fascinating, be it the soaring domes in Istanbul to the clean geometric lines characteristic of Tokyo. Whether you are interested in … Read more
- A Node.js-Powered App in Record TimeIn today’s developer case study, speed to market matters. The faster and better you can create a working application, the greater the chances of success. Node.js rapid app, through its flexibility, ease, and strong ecosystem, is rapidly becoming one of the top tools for setting development on a fast trajectory and evolving from delivery boy … Read more
- Open vs. closed models: AI leaders from GM, Zoom and IBM weigh trade-offs for enterprise useWant smarter insights in your inbox? Sign up for our weekly newsletters to get only what matters to enterprise AI, data, and security leaders. Subscribe Now Deciding on AI models is as much of a technical decision and it is a strategic one. But choosing open, closed or hybrid models all have trade-offs. While speaking … Read more
- Would you let AI plan your holiday itinerary?In his latest column, Jonathan McCrea is striking a lighter tone and telling us how AI has become his ideal travel companion. I’m heading away for a couple of weeks with the family. We’re going through the packing list now. Underwear, Calpol, flip flops, emergency sugar rations (for me, to be clear). The most important … Read more
Feature your latest articles
This sub headline is a text block global style that is larger and bolder.

Building AI-Powered SaaS Businesses – O’Reilly
View Article
Wikipedia volunteers spent years cataloging AI tells. Now there’s a plugin to avoid them.
View Article
Families at All Income Levels Struggle to Find Child Care
View ArticleKNOW MORE
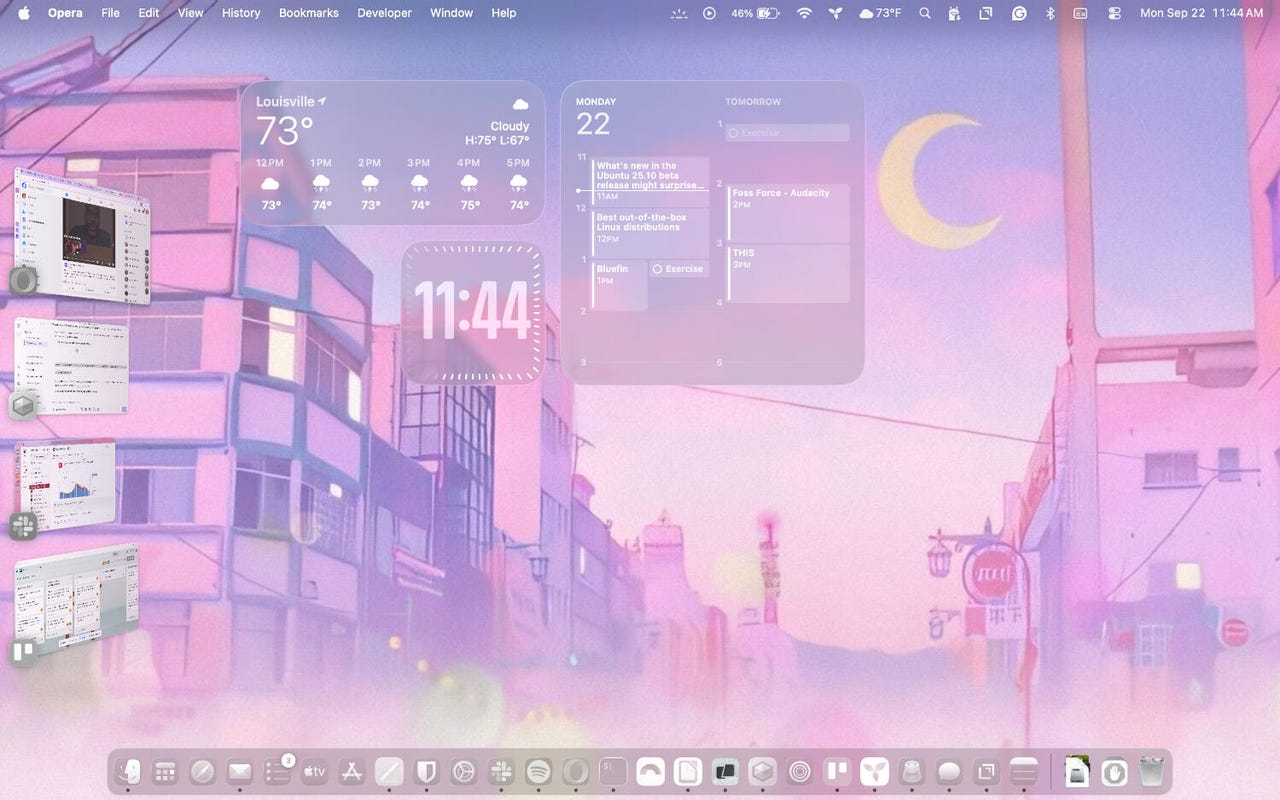
MacOS Tahoe finally turned me into a desktop widget user – here’s why
Jack Wallen/ZDNET Follow ZDNET: Add us as a preferred source on Google. ZDNET key takeaways If you’ve refused to use widgets, MacOS Tahoe may change your mind. Thanks to Liquid Glass, widgets are sexy again. Only add the widgets you need. Widgets aren’t exactly the most divisive topic in the tech-sphere, but for some, they are simply

Looking for a few good AI leaders – are you ready?
seksan Mongkhonkhamsao/Moment via Getty Images Follow ZDNET: Add us as a preferred source on Google. ZDNET’s key takeaways Rumors of 50% AI-related job cuts are greatly exaggerated. Leaders are needed to step up and keep AI efforts grounded. Vibe coding is the new citizen development. What is the biggest problem with AI today? It’s leadership. Good leaders

How to enable your Apple Watch’s Hypertension Detection feature – and why you should
Nina Raemont/ZDNET Apple’s Hypertension Detection feature could be the reason you learn about your high blood pressure. The feature is available on the latest lineup of Apple Watches that the tech giant unveiled earlier this month, but it’s also available on later models updated to WatchOS 26. Hypertension Detection recently received FDA clearance, validating the
The magnetic USB-C accessory I can’t live without – and why you need one too
Adrian Kingsley-Hughes/ZDNET Follow ZDNET: Add us as a preferred source on Google. ZDNET’s key takeaways These eliminate the risk of breaking a USB-C port. Most can carry 240W of power, 40Gb/s of data, and 8K@60Hz video. There are even breakaway connectors with power meters. The other day I was asked about my most recommended USB-C product. I’m
This iOS 26 trick made my old iPhone photos really pop – in 3D
How do Spatial Scenes differ from spatial photos and videos? Spatial Scenes are an AI-powered depth effect that turns 2D photos into dynamic, 3D-like images. They don’t require new hardware, because they use AI and software to add depth to any existing photo taken with an iPhone 12 or newer. Also: Why I’m skipping the iPhone
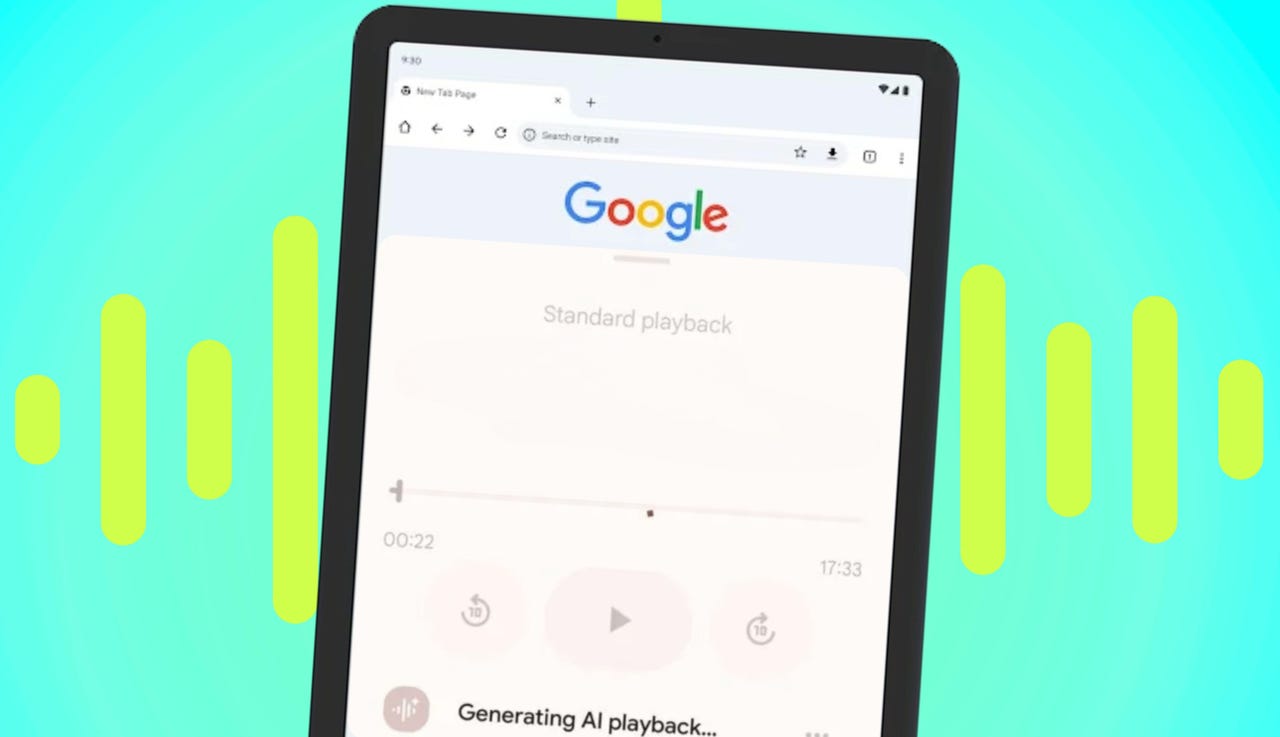
This new Chrome trick turn any web page into a podcast – how it works
Google / Elyse Betters Picaro / ZDNET Follow ZDNET: Add us as a preferred source on Google. ZDNET’s key takeaways Chrome for Android has a new feature in “Listen to this page.” Instead of traditional audio, you can hear a two-host podcast. The feature is now rolling out on a wide scale. If you use