
The Trillion Dollar Problem – O’Reilly
Picture this: You’re a data analyst on day one at a midsize SaaS company. You’ve got the beginnings of a data warehouse—some structured,…
Read More
She began with wedding decor, now her giant paper flowers tower all over S’pore
Koh Pei Li is a self-taught artist who creates elaborate paper flower installations If you’ve spotted massive, intricate floral installations at Gardens by…
Read More
5 plead guilty to laptop farm and ID theft scheme to land North Koreans US IT jobs
Each defendant also helped the IT workers pass employer vetting procedures. Travis and Salazar, for example, appeared for drug testing on behalf of…
Read More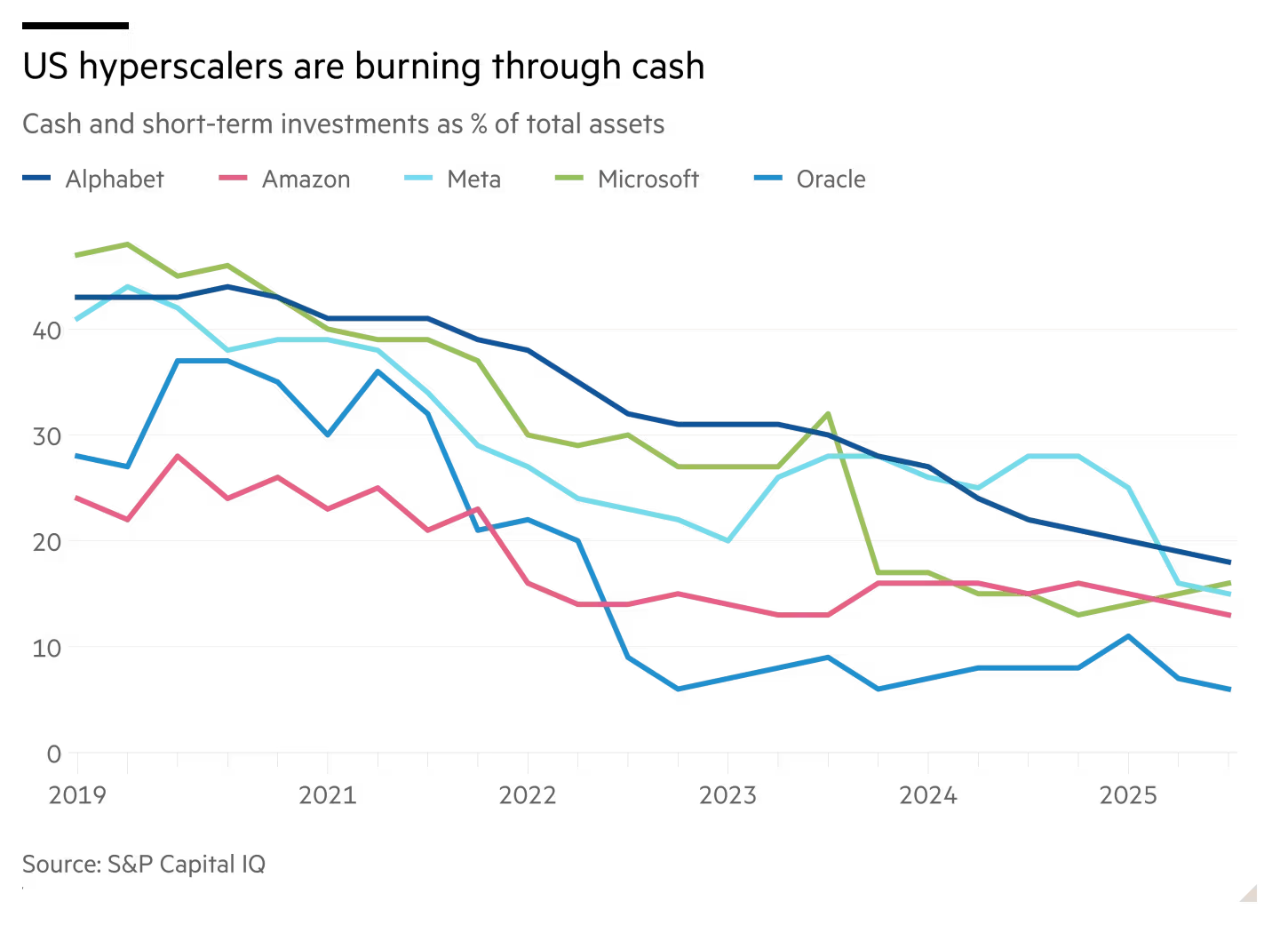
Oracle hit hard in Wall Street’s tech sell-off over its huge AI bet
“That is a huge liability and credit risk for Oracle. Your main customer, biggest customer by far, is a venture capital-funded start-up,” said…
Read More
NETGEAR Unveils Nighthawk 5G M7 Hotspot with eSIM Travel Router
NETGEAR today unveils its latest travel router, the Nighthawk 5G M7 Hotspot with eSIM (model MH7150). From the name, which is a mouthful…
Read More
Countering a Brutal Job Market with AI – O’Reilly
Headlines surfaced by a simple “job market” search describe it as “a humiliation ritual” or “hell” and “an emerging crisis for entry-level workers.”…
Read More
Laurence Moroney on AI at the Edge – O’Reilly
Generative AI in the Real World Generative AI in the Real World: Laurence Moroney on AI at the Edge Play Episode Pause Episode…
Read More
This is how SMEs & startups are using AI wrongly
AI is a powerful tool, but integration requires a broad rethinking, says Christopher Cai Disclaimer: Unless otherwise stated, any opinions expressed below belong…
Read More
After Years Reporting on Early Care and Education, I’m Now Living It
In August 2019, I walked into an early learning center in Philadelphia with a blank reporter’s notebook, a camera and a whole lot…
Read More
S’pore F&B group Creative Eateries acquired by Asia White Knight
Homegrown F&B group Creative Eateries has been acquired by Asia White Knight Group, an investment and operations group in the franchise sector. The…
Read MoreCategories
Latest Articles