
Chef-in-Box on turning vending smart with 500+ hot meal machines
Vending machines are ubiquitous in Singapore today, dispensing drinks, snacks, newspapers, and now even cars. However, the landscape was not this vibrant from…
Read More
Mediacorp lays off 93 employees in Singapore
Mediacorp is laying off 93 employees, or slightly over 3% of its total staff strength, to adapt to “the rapidly evolving media landscape and…
Read More
The Prive Group abruptly shuts all restaurants in Singapore
Singaporean F&B collective The Prive Group has closed all its restaurants in the city-state, with all operations ceasing on Aug 31. In a…
Read More
How fnp.sg became a go-to platform for gifting in S’pore
[Written in partnership with fnp.sg, but the editorial team had full control over the content.] If you’ve ever received a bouquet for a birthday,…
Read More
Zuckerberg’s AI hires disrupt Meta with swift exits and threats to leave
“While TBD Labs is still relatively new, we believe it has the greatest compute-per-researcher in the industry, and that will only increase,” Meta…
Read More
Google warns that mass data theft hitting Salesloft AI agent has grown bigger
Google is advising users of the Salesloft Drift AI chat agent to consider all security tokens connected to the platform compromised following the…
Read More
At 24, she left her job to sell S’pore’s 1st Sanrio-licensed macarons
At Sugarsmith, macarons aren’t just dainty French confections anymore, they’re transformed into miniature works of art. Hand-piped and meticulously crafted, the brand’s confections…
Read More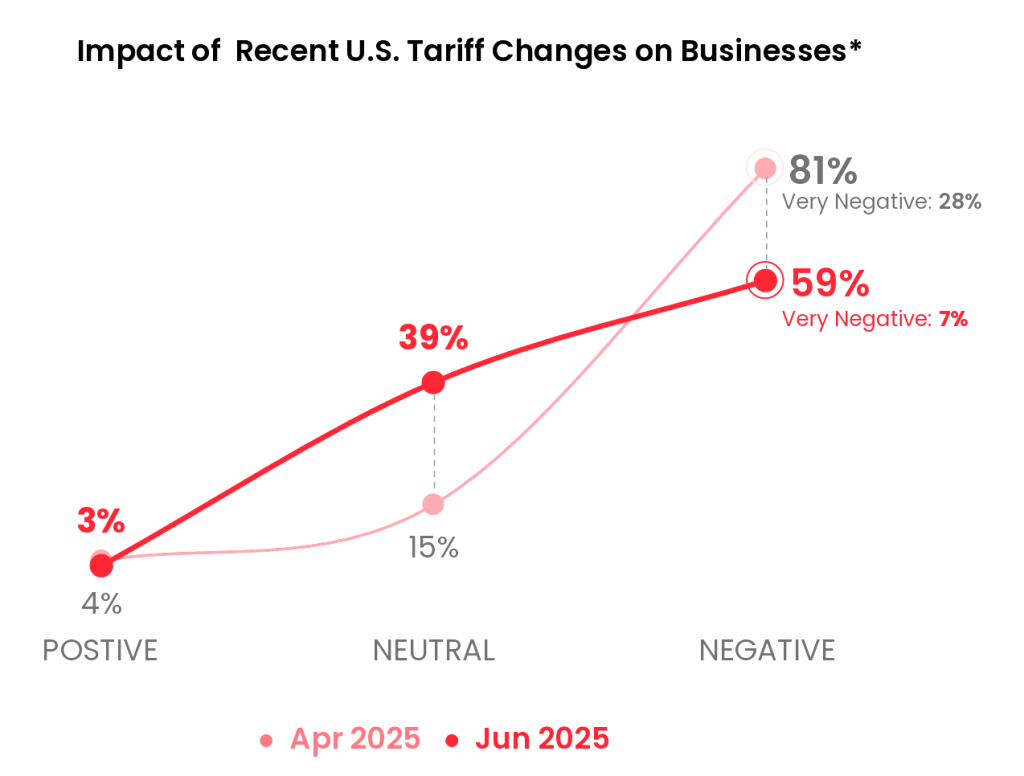
More S’pore companies to freeze wages & halt hiring
Disclaimer: Unless otherwise stated, any opinions expressed below belong solely to the author. Singapore Business Federation released its quarterly business sentiment survey yesterday (Aug 28)…
Read More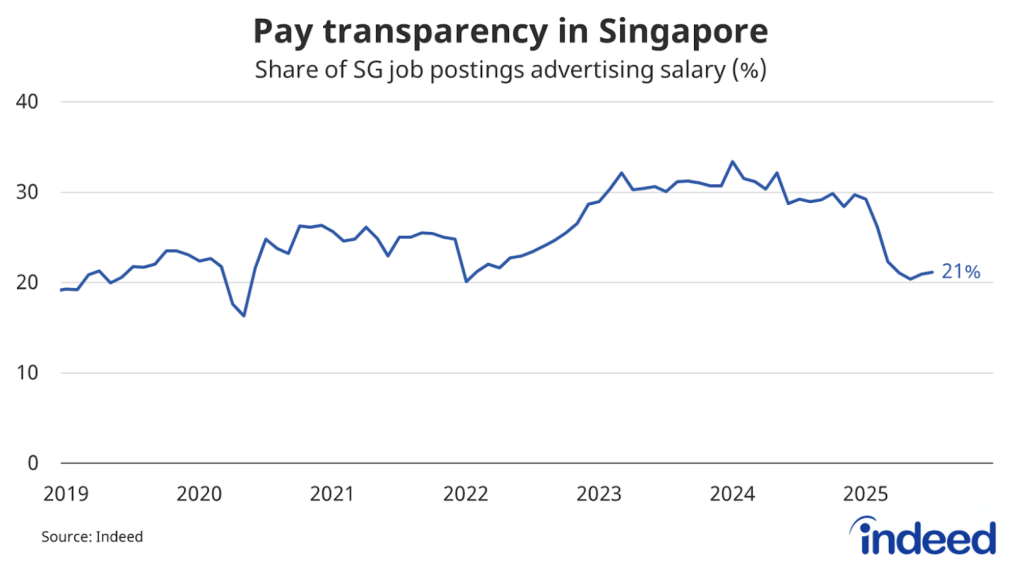
S’pore job postings suffer the biggest drop in 2 yrs
Disclaimer: Unless otherwise stated, any opinions expressed below belong solely to the author. One of the largest job listing portals, Indeed, has just…
Read More
Dual-band Wi-Fi 7 Mesh Systems: 2025’s Best Five
Below is the list of the current best dual-band Wi-Fi 7 mesh systems. These are hardware without the 6GHz band among those I’ve…
Read MoreCategories
Latest Articles