
What Is A Trim Router And How Do You Use It For Your Woodworking Projects?
Woodworking isn’t just about throwing giant saws around and rubbing power sanders on everything; sometimes you need…
Read More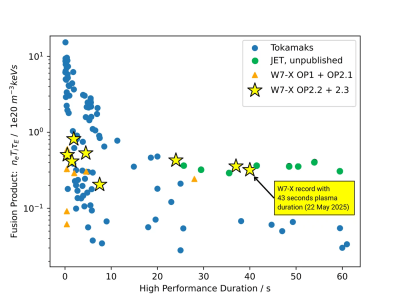
Wendelstein 7-X Sets New Record For The Nuclear Fusion Triple Product
Fusion product against duration, showing the Lawson criterion progress. (Credit: Dinklage et al., 2024, MPI for Plasma Physics) In nuclear fusion, the triple…
Read More
Apple Hornsby in Australia to close in October 2025
Apple will permanently shutter one of its Australian locations later this year, choosing to instead direct customers to a newly revamped store. Apple…
Read MoreAWS previews Kiro IDE for devs over vibe coding • The Register
Amazon Web Services has created what it’s calling an “agentic IDE” that it claims avoids the pitfalls of vibe coding. With the advent…
Read More
What Is A Tank Turn And How Does It Work On A Rivian?
While Rivian Automotive has technically been around since 2009, it has only become a legit player in…
Read More
US-made magnets, American investment, 500 million rare earth
As part of its already-announced US manufacturing effort, Apple is committing $500 million to a rare earth recycling firm, to develop new materials…
Read MoreAMD cleared to join Nvidia in selling AI chips to China • The Register
The US government has cleared AMD to resume exporting some accelerators to China. “We were recently informed by the Department of Commerce that…
Read More5 Underrated Tool Brands That Are Worth Reconsidering
101cats/Getty Images We may receive a commission on purchases made from links. Heading out to…
Read More
Ultimate Edition’ coming to the Mac on July 17
CyberPunk 2077: Ultimate Edition will be playable on the Mac starting July 17. On July 17, the futuristic, neon-lit world of Cyberpunk 2077…
Read MoreEx-soldier Googled “can hacking be treason?” pleads guilty • The Register
A former US Army soldier, who reportedly hacked AT&T, bragged about accessing President Donald Trump’s call logs, and then Googled “can hacking be…
Read MoreCategories
Latest Articles